
Oct 22, 2024 | Consulting, IT Security
Black Friday is a time of maximum expectation for companies, as it represents a unique opportunity to increase sales and attract new customers. However, with this increase in activity also comes a series of technological and cybersecurity risks that could compromise...

Sep 19, 2024 | Consulting, IT Security
In 1998, Pixar Animation Studios faced a monumental crisis during the production of “Toy Story 2.” A critical bug in the company’s servers erased nearly all of the project’s files, a devastating loss that threatened to delay the film and cause...
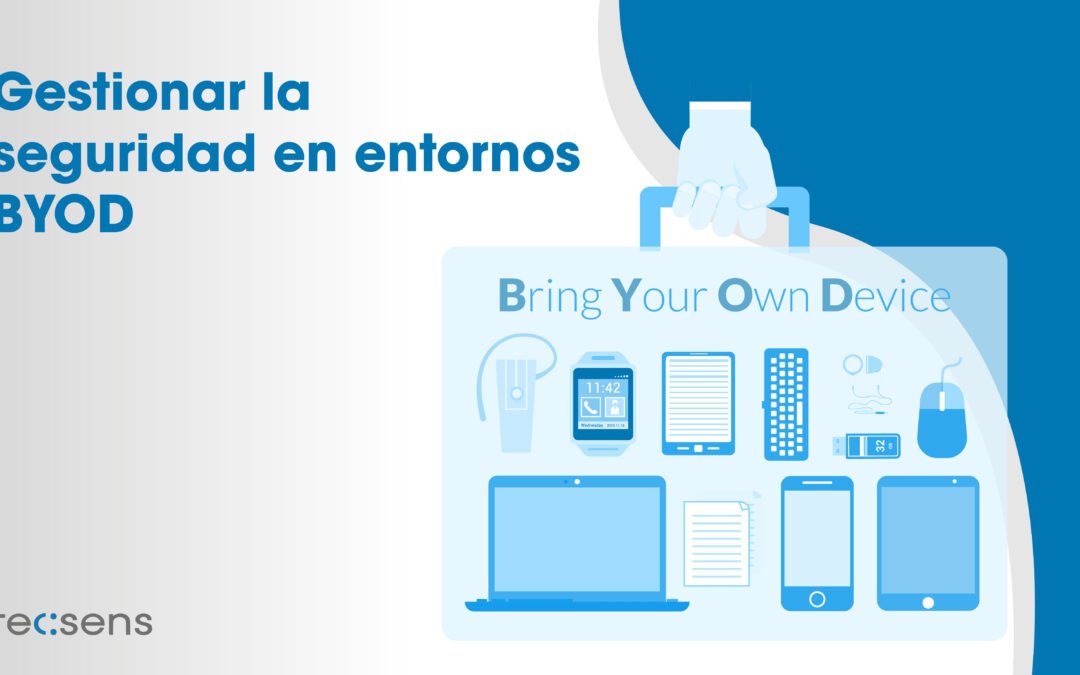
Apr 23, 2024 | Consulting, IT Security, Voice
Today, the concept of Bring Your Own Device (BYOD) has gained popularity in numerous organizations. This practice allows employees to use their own devices, such as smartphones, tablets, and laptops, to perform work tasks instead of relying solely on company-provided...

Dec 21, 2023 | Cloud, Consulting, IT Security
Cloud security is a growing concern, even for those with limited budgets. Fortunately, there are free tools that offer solid protection. In this article, we’ll examine and compare 5 free cloud security tools. Discovering 5 Free Cloud Security Tools 1. Cloudflare...
Oct 31, 2023 | Cloud, Consulting, IT Security
Health is a fundamental aspect in the life of any individual, and today, technology plays a crucial role in healthcare and information management. Disaster recovery is an essential practice in this field, as it ensures the availability and security of critical data in...
Oct 17, 2023 | Cloud, Consulting, IT Security
In the digital age in which we live, the importance of data backup has become fundamental in almost every aspect of our lives. We often associate backup with protecting important files on our electronic devices or crucial business data. However, we rarely consider the...










